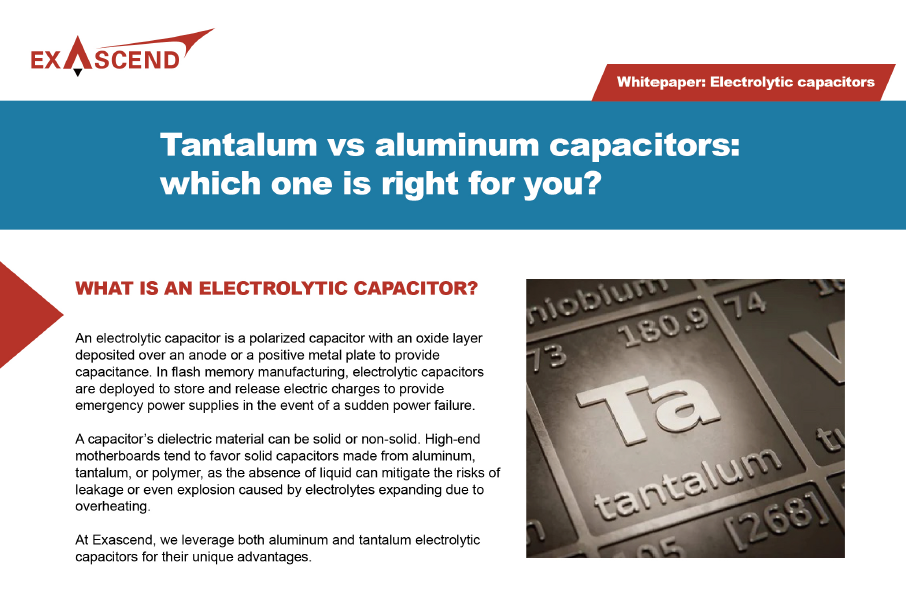
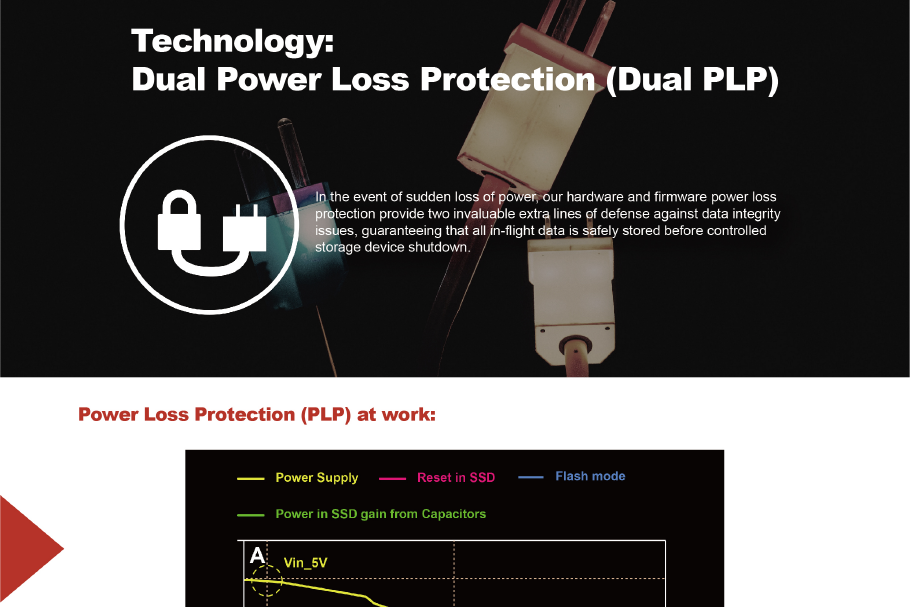
In the industrial and enterprise sectors, data security is an absolute necessity due to the rising complexity of data networks and increasing cyber threats. Self-encrypting drives (SEDs) play a crucial role in protecting sensitive information in these sectors. This blog explores how SEDs function and their significance in industrial and enterprise applications.
What Are Self-Encrypting Drives (SEDs)?
SEDs are specialized storage devices designed to automatically encrypt and decrypt data at the hardware level, ensuring data protection without user intervention. They are vital for scenarios where data integrity is paramount, particularly in industrial and enterprise settings.
How Self-Encrypting Drives Work
- Initialization and Key Generation: When deployed in an industrial or enterprise setting, an SED initiates key generation, creating encryption keys to safeguard your data.
- Data Encryption: When deployed in an industrial or enterprise setting, an SED initiates key generation, creating encryption keys to safeguard your data.
- Authentication: Access to encrypted data is meticulously controlled through authentication protocols, requiring authorized users to provide the correct credentials, such as passwords, smartcards, or biometrics.
Here, we use an Exascend SED with TCG Opal 2.0 as an illustrative example.
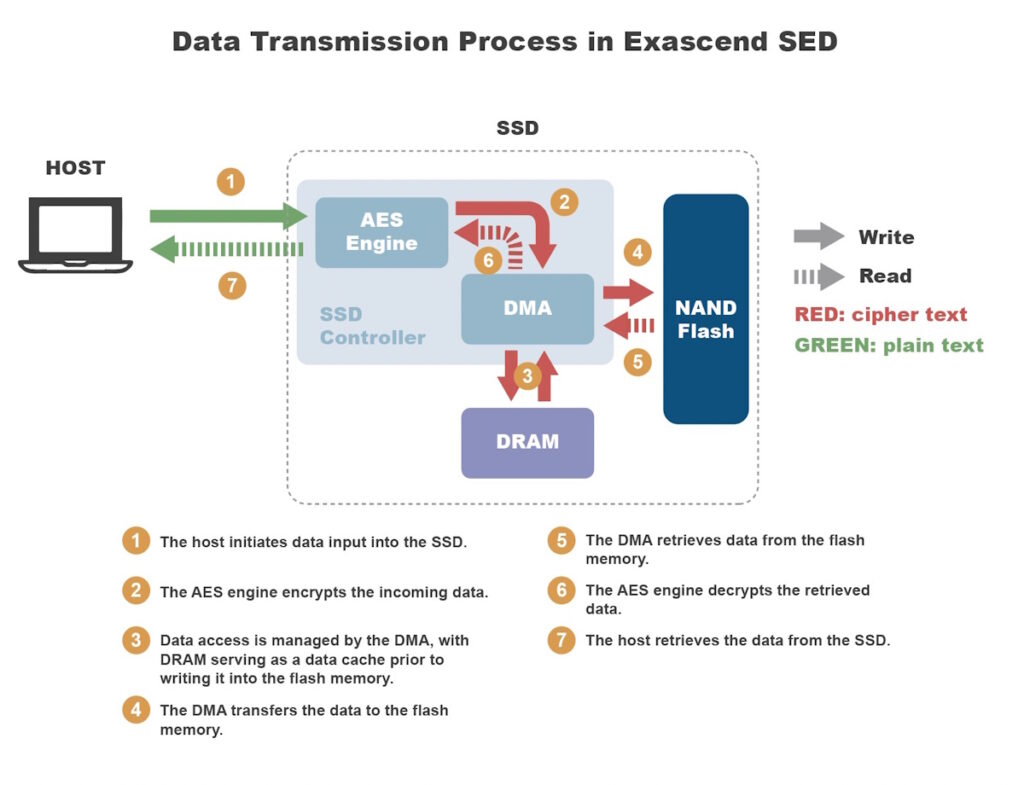
Key Management in Self-Encrypting Drives
Key management is crucial for SED security, with encryption keys typically securely stored within the drive. Some SEDs support key recovery and backup mechanisms to ensure data access even if a user forgets their password.
Security Measures and Features
SEDs come equipped with various security features tailored to industrial and enterprise sectors:
- Trusted Platform Module (TPM): Many SEDs incorporate TPM, a hardware-based security feature that enhances encryption key protection.
- Drive Locking and Secure Erase: SEDs offer remote drive locking and secure erase capabilities, rendering all data on the drive inaccessible.
- Anti-Brute Force Mechanisms: These measures deter potential intruders by thwarting repeated login attempts.
- Remote Management and Tracking: Some SEDs can be managed remotely, enabling real-time tracking of drive status and location.
Industrial and Enterprise Use Cases
SEDs are invaluable in a range of applications:
- Manufacturing: Protecting proprietary designs and manufacturing data from espionage.
- Healthcare: Ensuring patient data confidentiality in electronic health records.
- Finance: Safeguarding sensitive financial transactions and client information.
- Government: Protecting classified information and ensuring data sovereignty.
- Energy Sector: Securing critical infrastructure data against cyber threats.
Choosing the Right Self-Encrypting Drive
Selecting the appropriate SED for industrial and enterprise use involves considering specific security requirements, performance needs, and budget constraints. Leading manufacturers offer a variety of SED models tailored to different applications to ensure the perfect fit.
Setting Up and Managing Self-Encrypting Drives
Deploying SEDs in industrial and enterprise environments typically involves straightforward installation. However, adhering to best practices for key management and performing regular maintenance and security updates are crucial for sustained data protection.
Conclusion
In the high-stakes world of industry and enterprise, data security is not a luxury but a mandate. Self-encrypting drives (SEDs) offer a formidable defense against data breaches, providing the peace of mind necessary for these sectors to thrive. Whether safeguarding proprietary designs, patient records, or financial transactions, SEDs are the linchpin of data security.
As you strengthen your data security strategy, explore Exascend’s cutting-edge self-encrypting drive solutions. With a track record of excellence and innovation, Exascend’s SEDs are designed to meet the unique demands of industrial and enterprise applications. Discover the security, performance, and reliability that Exascend can bring to your organization’s data protection efforts.