Industrial and Enterprise SSD
Various Form Factors for Automotive, Industrial, and Enterprise Applications
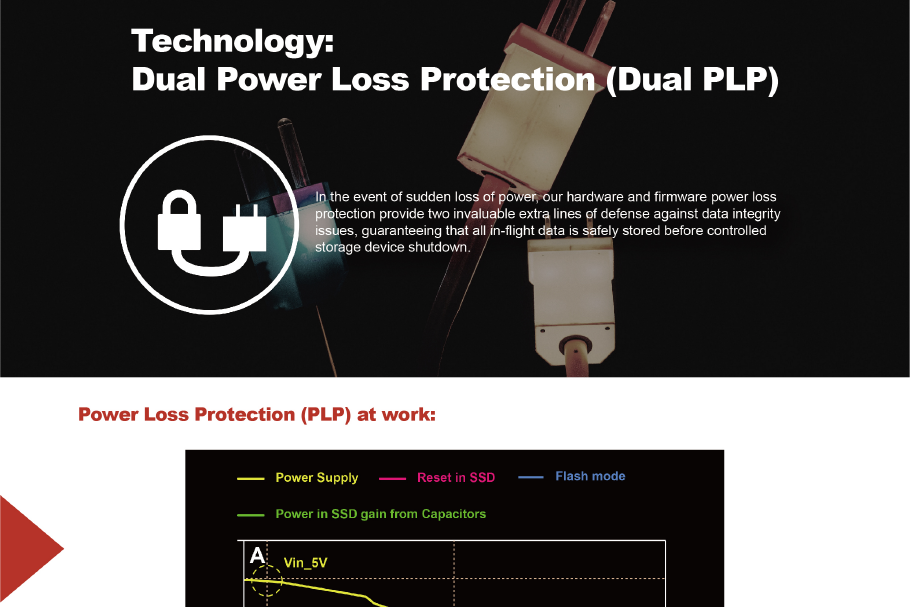
Exascend offers an expansive lineup of industrial-grade, enterprise-class, and self-encrypting SSDs meticulously crafted to cater to the diverse needs of automotive, industrial, and enterprise sectors. Our SSDs are engineered with cutting-edge technologies like Adaptive Thermal Control™ and SuperCruise™, ensuring unparalleled thermal management and write performance across a spectrum of environments. With RAID ECC technology and Dual Power Loss Protection (PLP), data integrity remains steadfast, even in the face of errors or sudden power disruptions.
Moreover, our SSDs prioritize power efficiency through meticulous control over hardware, firmware, and manufacturing processes, resulting in optimized performance tailored to the unique demands of specific applications. Security is paramount, with features such as TCG Opal 2.0, AES-256 encryption, secure erase, pre-boot authentication (PBA), and tamper-proof firmware options, providing robust safeguards for sensitive data.
For added resilience against environmental challenges like humidity, shock, and vibration, select products adhere to MIL-STD-810 standards and feature conformal coating and underfill technologies. With complete mastery over hardware and firmware solutions, we collaborate closely with clients to deliver bespoke SSD solutions that precisely align with their individual requirements, ensuring maximum efficiency, reliability, and security.
M.2 NVMe
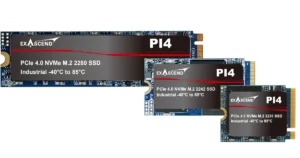
- PCIe Gen4 x4 / NVMe 1.4
- M.2 2280, 2242
- 176-layer 3D TLC NAND
- 960GB to 7.68TB
- Up to 3,200 MB/s sustained performance
- Op. Temp -40°C to 85°C
- Rad-Hard. Conformal Coating. Underfill.
- PCIe Gen4 x4 / NVMe 1.4
- M.2 2280, 2242, 2230
- 176-layer 3D TLC NAND
- 240GB to 7.68TB
- Up to 3,200 MB/s sustained performance
- Op. Temp -40°C to 85°C
- Conformal Coating. Underfill.
- PCIe Gen4 x4 / NVMe 1.4
- M.2 2280, 2242, 2230
- 176-layer 3D TLC NAND
- 240GB to 7.68TB
- Up to 3,200 MB/s sustained performance
- Op. Temp -40°C to 85°C
- PCIe Gen4 x4 / NVMe 1.4
- M.2 2280, 2242, 2230
- 176-layer 3D TLC NAND
- 240GB to 7.68TB
- Up to 3,200 MB/s sustained performance
- Op. Temp 0°C to 70°C
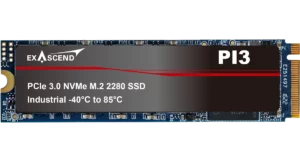
- PCIe Gen3 x4 / NVMe 1.2
- M.2 2280
- 3D TLC NAND
- 240GB to 3.84TB
- Up to 3,100 MB/s sustained performance
- Op. Temp -40°C to 85°C
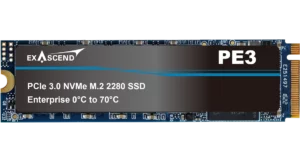
- PCIe Gen3 x4 / NVMe 1.2
- M.2 2280
- 3D TLC NAND
- 240GB to 3.84TB
- Up to 3,200 MB/s sustained performance
- Op. Temp 0°C to 70°C
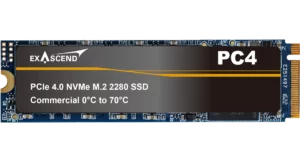
- PCIe Gen4 x4 / NVMe 1.4
- M.2 2280
- 176-layer 3D TLC NAND
- 1TB to 2TB
- Up to 3,500 MB/s sustained performance
- Op. Temp 0°C to 70°C
- PCIe Gen3 x4 / NVMe 1.2
- M.2 2280
- 3D TLC NAND
- 512GB to 4TB
- Up to 3,100 MB/s sustained performance
- Op. Temp 0°C to 70°C
U.2/U.3 NVMe
- PCIe Gen4 x4 / NVMe 1.4
- U.2 (7mm)
- 176-layer 3D TLC NAND
- 960GB to 15.36TB
- Up to 3,500 MB/s sustained performance
- Op. Temp -40°C to 85°C
- Rad-Hard. Conformal Coating. Underfill.
- PCIe Gen4 x4 / NVMe 1.4
- U.2 (7mm)
- 176-layer 3D TLC NAND
- 960GB to 15.36TB
- Up to 3,500 MB/s sustained performance
- Op. Temp -40°C to 85°C
- Conformal Coating. Underfill.
- PCIe Gen4 x4 / NVMe 1.4
- U.2 (7mm)
- 176-layer 3D TLC NAND
- 960GB to 15.36TB
- Up to 3,500 MB/s sustained performance
- Op. Temp -40°C to 85°C
- PCIe Gen4 x4 / NVMe 1.4
- U.3 (15mm)
- 176-layer 3D TLC NAND
- 6.4TB to 30.72TB
- Up to 7,100 MB/s sustained performance
- Up to 1,600K IOPS 4K random read
- Op. Temp 0°C to 70°C
- PCIe Gen4 x4 / NVMe 1.4
- U.2 (7mm)
- 176-layer 3D TLC NAND
- 960GB to 15.36TB
- Up to 3,500 MB/s sustained performance
- Op. Temp 0°C to 70°C
- PCIe Gen3 x4 / NVMe 1.2
- U.2 (7mm)
- 3D TLC NAND
- 480GB to 7.68TB
- Up to 3,100 MB/s sustained performance
- Op. Temp -40°C to 85°C
- PCIe Gen3 x4 / NVMe 1.2
- U.2 (7mm)
- 3D TLC NAND
- 480GB to 7.68TB
- Up to 3,200 MB/s sustained performance
- Op. Temp 0°C to 70°C
- PCIe Gen3 x4 / NVMe 1.2
- U.2 (7mm)
- 3D TLC NAND
- 1TB to 4TB
- Up to 3,100 MB/s sustained performance
- Op. Temp 0°C to 70°C
EDSFF
- PCIe Gen4 x4 / NVMe 1.4
- E1.S (5.9mm/9.5mm with enclosure)
- 176-layer 3D TLC NAND
- 960GB to 7.68TB
- Up to 3,500 MB/s sustained performance
- Op. Temp -40°C to 85°C
- Rad-Hard. Conformal Coating. Underfill.
- PCIe Gen4 x4 / NVMe 1.4
- E1.S (5.9mm/15mm with enclosure)
- 176-layer 3D TLC NAND
- 960GB to 7.68TB
- Up to 3,500 MB/s sustained performance
- Op. Temp -40°C to 85°C
- Conformal Coating. Underfill.
- PCIe Gen4 x4 / NVMe 1.4
- E1.S (5.9mm/15mm with enclosure)
- 176-layer 3D TLC NAND
- 960GB to 7.68TB
- Up to 3,500 MB/s sustained performance
- Op. Temp -40°C to 85°C
- PCIe Gen4 x4 / NVMe 1.4
- E1.S (5.9mm/15mm with enclosure)
- 176-layer 3D TLC NAND
- 960GB to 7.68TB
- Up to 3,500 MB/s sustained performance
- Op. Temp 0°C to 70°C
M.2 SATA
- SATA 6.0Gb/s
- M.2 2280
- 176-layer 3D TLC NAND
- 240GB to 7.68TB
- Up to 550 MB/s sustained performance
- Op. Temp -40°C to 85°C
- Conformal Coating. Underfill.
- SATA 6.0Gb/s
- M.2 2280
- 176-layer 3D TLC NAND
- 240GB to 7.68TB
- Up to 550 MB/s sustained performance
- Op. Temp -40°C to 85°C
- SATA 6.0Gb/s
- M.2 2280
- 176-layer 3D TLC NAND
- 240GB to 7.68TB
- Up to 550 MB/s sustained performance
- Op. Temp 0°C to 70°C
- SATA 6.0Gb/s
- M.2 2280
- 3D TLC NAND
- 240GB to 7.68TB
- Up to 550 MB/s sustained performance
- Op. Temp -40°C to 85°C
- SATA 6.0Gb/s
- M.2 2280
- 3D TLC NAND
- 256GB to 2TB
- Up to 550 MB/s sustained performance
- Op. Temp 0°C to 70°C
2.5" SATA
- SATA 6.0Gb/s
- 176-layer 3D TLC NAND
- 240GB to 7.68TB
- Up to 550 MB/s sustained performance
- Op. Temp -40°C to 85°C
- Conformal Coating. Underfill.
- SATA 6.0Gb/s
- 176-layer 3D TLC NAND
- 240GB to 7.68TB
- Up to 550 MB/s sustained performance
- Op. Temp -40°C to 85°C
- SATA 6.0Gb/s
- 176-layer 3D TLC NAND
- 240GB to 7.68TB
- Up to 550 MB/s sustained performance
- Op. Temp 0°C to 70°C
- SATA 6.0Gb/s
- 3D TLC NAND
- 240GB to 7.68TB
- Up to 550 MB/s sustained performance
- Op. Temp -40°C to 85°C
mSATA
- SATA 6.0Gb/s
- 176-layer 3D TLC NAND
- 240GB to 960GB
- Up to 550 MB/s sustained performance
- Op. Temp -40°C to 85°C
- Conformal Coating. Underfill.
- SATA 6.0Gb/s
- 176-layer 3D TLC NAND
- 120GB to 960GB
- Up to 550 MB/s sustained performance
- Op. Temp -40°C to 85°C
- SATA 6.0Gb/s
- 3D TLC NAND
- 120GB to 960GB
- Up to 550 MB/s sustained performance
- Op. Temp -40°C to 85°C